Google Play Store Warning-Find And Delete All Apps On This List


Here we go again. A list of malicious apps has just been published and smartphone users are being urged to root out and delete any still on their devices. The latest report outs more than 350 apps responsible for more than a billion ad bid requests per day.
This latest report comes courtesy of Human Security’s Satori team, which says it has “disrupted IconAds, a massive fraud operation involving hundreds of deceptive mobile apps that hide their presence and deliver unwanted ads.” this app campaign has been under investigation for some time, but is growing its viral presence.
Satori says this “highlights the evolving tactics of threat actors,” and that the scale of threats such as this are similar to BADBOX 2.0, the major IOT threat flagged by the FBI and Google, in which millions of smart TVs and other devices
Here is the list of IconAds issued by Human; and here is the list of previously known apps flagged by other researchers before this latest report was published.
This AdWare follows on the HiddenAds threat, but on a much larger scale. The malware takes over devices with unwanted fullscreen ads, generating revenue for its handlers. It even changes app icons top avoid detection and removal.
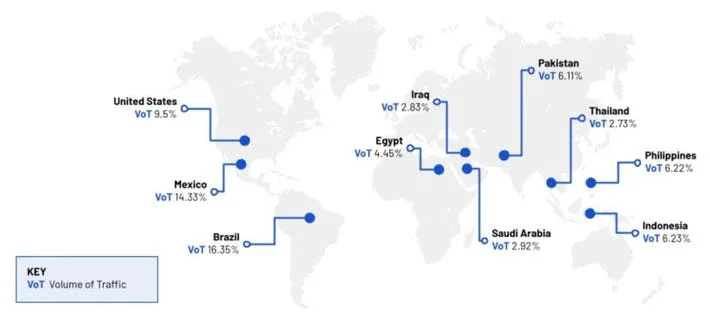
“While these apps often have a short shelf life before they’re removed from Google’s Play Store,” Sartorial says, “the continued new releases demonstrate the threat actors’ commitment to further adaptation and evolution.
Google has now deleted all of apps in the report fromPlay Store, and users with Play Protect enabled will be protected from those apps. But apps are not automatically deleted from devices, and so you should do this manually.
In Satori’s technical report, it warns that such is the scale of this operation it deployed a dedicated domain for every malicious app, which helped the team compile their list.
“These domains consistently resolve to a specific CNAME and return a specific message; this means that while the domains were different, they very likely shared the same back-end infrastructure or second-level C2. These and other unique parameters allowed Satori researchers to find more of these domains and associate them back to IconAds.”
The team also warns that the app obfuscation was highly deceptive. In one instance, an app “used a variation of the Google Play Store’s own icon and name. When opened, it automatically redirects into the official app while working in the background.”
Satori says “the IconAds operation underscores the increasing sophistication of mobile ad fraud schemes. Ongoing collaboration across the digital advertising ecosystem is essential to disrupting these and future fraud operations.”





